.
All SPAM is
NOT Harmless Junk!
It
can steal your infomration or even wipe out your files . . . learn to recognize
and avoid coded links, trojans & viruses
 Free
stuff, CLICK HERE! Free
stuff, CLICK HERE!
The Trojan Horse has been used for millennia as a symbol for anything disastrous that is disguised as something desirable, such as the tricks on this page. Coded Links... I recently received an email that read "Could you please be so kind as to click renew by Friday" from an unfamiliar site. The link contained codes like: id=534467. It also contained my domain name. What does this mean? The link points to a script,
not a text page, and these are parameters. They tell the spammer
your address was real, meaning you'll get more spam.
next column |
How coded
links work
Say you get an email advertising widgets, and it says click here for widgets. Hold the mouse over that link and you'll see the hidden link text in your browsers status line, and you'll see it contains an email address. But it might not be so easy to recognize, something like joe%40hotmail.com, or even 14357bdLIHx. The link goes to a script which can read the link parameters and record them in a database. The point I'm not trying to make you
paranoid to click on a link. Just aware. In your sacrificial
bait
& switch account, click away! But be very careful in your
serious mail account. And in your serious account it is much easier
to view the link text and see if there are any mysteriously unexplained
parameters. next article below |
 Web
Site Attacks? Web
Site Attacks?
Maybe we are slightly paranoid, you are thinking by now, but get this . . . during the fall of 2001, starting about mid September and continuing until we abandoned our primary business email address, we got from 3 to 7 messages per week from unidentified sources, mostly overseas, with roughly 100 kb attachments. When some routing information
was available, the message was likely to have originated in former communist
block countries, or middle eastern countries. Some messages appeared
to originate in the United States. We carefully avoided opening any
of the attachments. |
Inducement
Each message was different. One with the subject "a good tool" appeard to be some type of CAD (computer aided design or drafting) program. This kind of software is usually expensive. Here was a free one. It was tempting. One message subject proclaimed "Mail delivery failed: returning message to sender" from "Mail Delivery System." Hmm, who did I send a message to that failed? After opening it using a webmail reader, I realized the message contained no text and was a Windows program. If I had openend it on my PC, doubtless it would have wiped the hard drive clean, saving me the trouble of ever having to delete a file to free up space! Another fake returned message
was even more clever, pretending to have an image attached, see figure. |
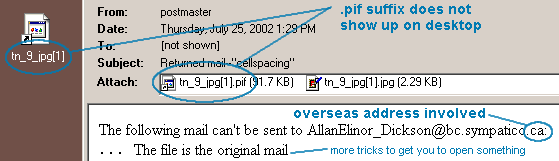
| Telltale
Signs
In the illustration above, you have all of the telltale signs except a free stuff offer. This message attempts to be very, very tricky.
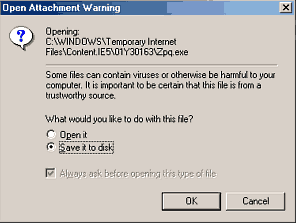
(one of them actually is a harmless image) (even if you didn't notice the attachment was an executable, how could the original email be in an image file? - ALWAYS turn on the option to view file extensions! - see Windows help file) If you use Microsoft Outlook, make sure you have version 5 or later, and configure it NOT to automatically open attachments. You'll ordinarily get a window that looks something like this:
I always click cancel. NEVER click "open it." If it is from someone you know, ask if they meant to send it, then save it to disk and scan it with a virus scanner. After 6 months I decided not to ignore these anymore. My curiosity was aroused. Were they related? I unblocked the address they were coming to and began to collect them, being careful not to open any attachments. |
What was
that attachment?!
Of course, I scanned them with a virus scanner. 100% of this batch of attachments, although many details of the message and length were different, were identified as the W32.Klez.H@mm worm. You can read on the Symantec site all the nasty things this thing does, how it disables your virus scanner, and so forth, and debate with your friends the subtleties of virus vs. trojan vs. worm. But the bottom line is: it will trash your computer, and send emails from you to all your friends attempting to persuade them to trash their computers. Beware of stealth trojans, either in attachments or software you download. These are relataively new, inspired by full-time broadband interenet connections. They appear to perform some useful function, but really scan your computer for personal information and affect your online transactions. They may steal from you, or from those you do business with, such as ad-supported software that steals referral commissions at shopping sites. If you continue to leave your serious email address unguarded, out there for all to see, the one where you have to process email fast & furious to get through it, how long will it be before you forget, are tired and get fooled for a moment, and click on one of these things and - voila! - you get to spend the next two days restoring your computer and finding out whether you really backed everything up! Not me. My OS gets deleted often enough through my own mistakes. I don't need help from a virus, worm, whatever. I use a contact form, a separate address for business, and I change the address every time I get a suspicious attachment. |